Fleet telematics is one of the most important aspects of operating a modern business. Supply chain bottlenecks, such as delays and damaged goods, cost companies a substantial amount of money every year and telematics mitigates those risks. Unfortunately, connected vehicles present potential security vulnerabilities that bad actors may take advantage of. ABI Research recently looked at how Vehicle Manufacturers (VMs), which fall under the sphere of Original Equipment Manufacturers (OEMs) in the automotive industry, keep their telematics data secure in the Secure Data Management in Automotive Telematics research analysis report.
What Is Telematics?
To put it simply, telematics is the tracking of assets like vehicles, pallets, containers, etc. Telematics systems monitor vehicle location, vehicle speed and position, mileage, fuel, emissions, air pressure, the temperature of perishable products, and other key data. Using this information, supply chain workers can take action to avoid product contamination, identify maintenance issues, and create more efficient routes. Telematics devices are installed in the vehicle either during the manufacturing process or later using a third-party manufacturer.
For fleet telematics systems to work, there also needs to be reliable connectivity over the cloud, so that information can be sent and received. While 3G/4G are the most common connectivity choices for automotive telematics right now, 5G is well on its way to becoming the dominant option. Software platforms like FleetUp and Intellias enable fleet management personnel to visualize real-time analytics.
Fleet Management Security Starts at the IC Level
Embedded Secure Elements (eSEs) prevent tampering and unauthorized access, while also storing sensitive data that are cryptographically protected. eSEs are either installed on a device’s Integrated Circuit (IC) and chip, along with the Embedded Universal Integrated Circuit Card (eUICC) and Embedded Subscriber Identity Module (eSIM), or they’re separate components in the Telematics Control Unit (TCU).
It’s generally agreed that those eSEs take care of the bulk of cellular security. However, as vehicles become more software-oriented, there are concerns about remote updates and the security of an Original Equipment Manufacturer’s (OEM) backend. To address the latter fleet telematics issue, companies like Thales use specialized firmware applets that open up support for security-bolstering features, such as a Virtual Private Network (VPN) that establishes a more secure cloud connection to the vehicle.
Trusted Platform Modules for Boosted Fleet Telematics Safety
A Trusted Platform Module (TPM) is a chip installed in the motherboard of PCs, laptops, mobile phones, network equipment, and Internet of Things (IoT) devices. TPMs ensure platform integrity by authenticating artifacts, such as passwords, certificates, and encryption keys. The four main categories of TPMs are as follows:
- Discrete TPM: Most typically found in PCs, discrete TPMs offer the most robust security solution for fleet telematics devices. This method is designed to withstand the most sophisticated attacks that hackers attempt.
- Integrated TPM: This is the second most robust security solution among TPMs and is integrated into a chip, instead of being a separate component. Although integrated TPMs offer competent security, they are not tamper-proof for the laptops, printers, modems, gateways, and IoT devices in which they’re usually found.
- Firmware TPM: Firmware TPM processes involve a code to run on the main Central Processing Unit (CPU), so chip integration is not needed. The code runs through a secure program that’s separate from other CPU programs called a Trusted Execution Environment (TEE), making it exponentially more challenging for hackers to access sensitive information like private keys. The cons of firmware TPMs are that, like integrated TPMs, they are not tamper-proof, and they rely on the functionality and investment of other components like the TEE Operating System (OS).
- Software TPM: Software TPMs are the most vulnerable of all main types of TPMs, including bugs in the OS. But software TPMs do have their use in the testing phase of an OEM’s car prototype where security isn’t as prioritized yet.
ABI Research has found that integrated and firmware TPMs are the most prevalent in connected vehicles. Discrete TPMs will be mostly exclusive to the luxury segment, while software TPMs, as previously mentioned, are suitable for testing purposes.
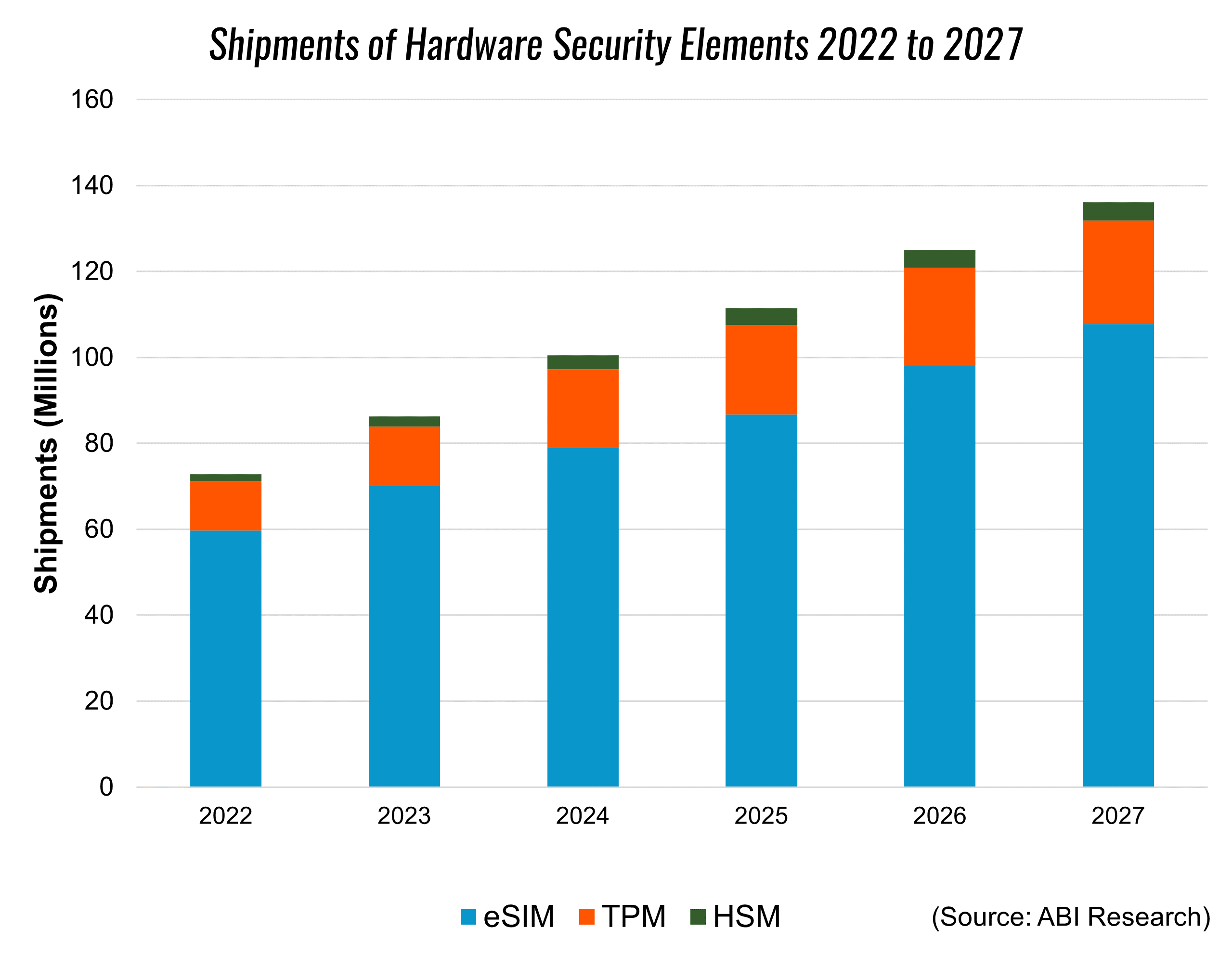
More Focus Areas
Fleet telematics involves a wide range of devices and an astounding volume of real-time data being collected, transmitted, and analyzed. All these devices and processes need effective cybersecurity applications for stakeholders to have peace of mind that hackers won’t be able to tamper with vehicle mobility functions and steal confidential information. The IC/chip level and TPMs are two areas for OEMs to prioritize in fleet management solutions, and for supply chain leaders to consider when weighing options.
Other considerations include Hardware Security Modules (HSMs), firewalls, Intrusion Detection and Prevention Systems (IDSPs), vehicle communications, and Firmware Over-the-Air (FOTA). To learn more about all these fleet management security concerns, download ABI Research’s Secure Data Management in Automotive Telematics research analysis report.
Related Content:
Ranking the Top 5 Leading Fleet Telematics Companies [blog]
8 Best Practices for Improving Fleet Management [blog]
6 of the Most Essential Fleet Management KPIs That Will Boost Your Bottom Line [blog]
Commercial Vehicle Telematics Market Update [blog]
Is Your Fleet Management Plan Factoring in These Compelling Strategies? [Research Highlight]

