Virtually every industrial sector is digitally transforming. As more connected devices are introduced to work environments, this exposes the Industrial Control System (ICS) to more cyber risks. The challenge is that ICS components are not suited for communication over the Internet. Making matters worse, the operating technology and software that industrial operators use don’t receive enough patches for threat protection—out of fear of downtime.
These security challenges are all compounded by the fact that many communication protocols used in industrial settings are insecure. Needless to say, the industrial control system environment presents a ripe opportunity for threat actors to steal production data or take command of machinery.
In this article, you’ll get a fleshed-out guide on everything ICS cybersecurity, including the following takeaways:
- What an ICS is and the components that are integral to the system
- What ICS security is and the business goal of its application
- Common ICS protocols that are vulnerable to a cyberattack
- Biggest threat actors of industrial control systems
- How the ICS is attacked
- Best practices to secure ICS endpoints and networks
What Is an ICS?
An Industrial Control System (ICS) refers to the various hardware and software used to manage, regulate, and automate industrial processes. The ICS includes physical devices, networks, systems, and other technologies supporting industrial operations. These systems are essential in manufacturing, transportation, water and energy utilities, and other critical sectors. You can think of the ICS as the nucleus of mission-critical operations, providing greater control over machinery and industrial processes.
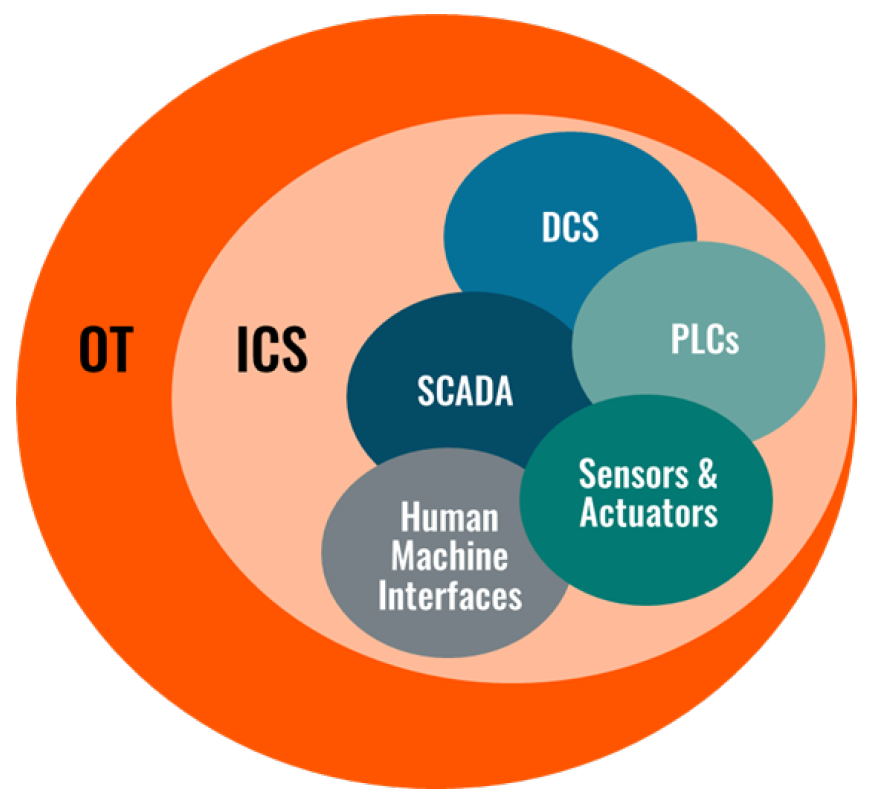
The major components of an ICS system include the following:
- Supervisory Control and Data Acquisition (SCADA) systems efficiently manage and control dispersed industrial equipment.
- Distributed Control Systems (DCSs) are similar to SCADA systems in that they control and monitor industrial assets and processes.
- Programmable Logic Controllers (PLCs) are considered one of the most important components of the ICS environment. They have widespread usage in automating industrial processes and collecting data for analysis and industrial optimization.
- Human-Machine Interfaces (HMIs) are graphic user interfaces with which humans can interact with ICS devices and processes.
- Sensors are used to measure parameters, such as temperature, pressure, humidity, flow rate, and other vital industrial variables.
- Actuators receive data sent from sensors to PLCs and other devices in the ICS and then control physical processes based on the processed data sent back to them.
The figure below, created by ABI Research, depicts the ICS environment.
What Is ICS Security?
ICS security is defined as the organizational efforts to protect the devices, components, and networks used in an industrial control system from cyberattacks. Every connection within an industrial control system, from a handheld Internet of Things (IoT) device to a smart sensor, introduces another potential ICS network entry point. ICS cybersecurity best practices involve a range of hardware and software solutions that make it far more difficult to infiltrate the system and notify personnel of attempted breaches.
Related Content
9 Accomplished ICS Cybersecurity Companies That Can Protect Your Industrial Operations from Attacks
Common ICS Protocols Vulnerable to Cyberattacks
Something to be mindful of is that many ICS protocols are highly vulnerable to cyberattacks. These protocols were not developed with security in mind, so they offer an excellent way for threat actors to infiltrate the ICS network.
ABI Research has identified the following commonly used protocols as being susceptible to ICS security breaches:
- Modbus
- DNP3
- Profinet
- S7COMM
To find out why these protocols are vulnerable to ICS attacks and what solutions are being implemented to harden these protocols, download the report.
ICS Threat Actors
Phishing, malware, ransomware, and other cybersecurity attacks on an ICS can come from a wide range of sources.
- Internal threats to the industrial control system could stem from employee negligence, poor ICS cybersecurity training, and suppliers/contractors.
- External threats to ICSs come from nation-states, hacktivists, cybercrime groups, and competitors.
Regardless of who the threat actor is, they know that hitting the ICS could result in operational downtime—and subsequent loss of productivity. If the attack is on a utility provider, the result could be power outages or heat loss in people’s homes.
While a state-backed attack on an ICS may be motivated by geopolitical tensions, other attacks are often financially motivated. This can come in the form of ransoms or damage to a competing company’s brand reputation.
How the ICS Is Attacked
An ICS attack can target a variety of components of the system, beginning with the network or endpoint devices at the highest level.
- Attack on the Network: When critical infrastructure is the prime target, the cybercriminal will attack the connection residing between ICS devices and the SCADA system. Alternatively, the attacker might try to intercept data in motion. As a few examples, this kind of ICS attack could mean the attacker eavesdrops on network traffic, interrupts network communications, or takes advantage of device vulnerabilities.
- Theft of Sensitive Information: A cyberattack on an industrial control system could also involve the theft of sensitive information, such as system configurations, production data, or personal information of employees and customers. The attacker would target the data stored within ICS systems to steal information.
- Exploitation of Endpoints: Virtually all ICS endpoints are potential attacker exploits. In this case, the attacker targets applications, systems, or devices connected to the industrial control network. Examples include PLCs, Remote Terminal Units (RTUs), HMIs, and SCADA systems.
Through various interviews with industrial organizations and cybersecurity vendors, ABI Research has identified a multitude of ICS security best practices. The rest of this article provides some of the most effective ICS security measures.
How to Secure ICS Endpoints
In this section, I’ll explain some ICS security solutions that effectively protect ICS endpoints from cyber threats.
Safeguarding Legacy Technologies
Given the long life spans of an industrial control system, hardening the security layer of legacy ICS equipment is key. To secure legacy ICS network endpoints, industrial companies can use the following methods and strategies:
- Segment the legacy ICS by using industrial firewalls, Virtual Local Area Networks (VLANs), and air gapping techniques. This will limit access to critical infrastructure.
- Shrink the attack surface by disabling unnecessary devices and network connection protocols.
- Improve authentication by implementing access control, strong passwords, or Multi-Factor Authentication (MFA) for questionable, unverified, or untrusted devices and platforms.
- Conduct regular security assessments for legacy ICSs to help identify weak points. That will enable you to apply appropriate security measures, including patching where possible.
Identity, Authentication, and Access Management Technologies
As critical infrastructure firms digitally transform their operations, digital Identity Access Management (IAM) technologies are gaining popularity for safeguarding ICSs.
Trusted Platform Modules (TPMs) are also a mainstay for ICS security. The usefulness of TPMs in industrial control system security is in their ability to store cryptographic keys securely. TPMs authenticate devices and verify that the firmware and software within the ICS environment can be trusted.
Proper Device Onboarding
Using the pre-configured credentials of ICS components is not advisable. If, for example, your organization receives a shipment of PLCs, be sure to change their credentials and configure them before putting them to use. Having stronger passwords is a critical enabler in protecting industrial control systems.
Proper device onboarding is also essential for integrations and functionality within the ICS. When devices are not adequately onboarded, there’s a greater risk of display communication issues with other devices in the ICS environment.
Patch Management and Hot Patching
With cyber threats on the rise, updating and patching the devices and networks associated with your ICS is one of the best ways to circumvent attacks from malicious actors. You must:
- Identify where vulnerabilities lie in your ICS network.
- Conduct a detailed inventory of all ICS devices.
- Consider hot patching to avoid operational downtime when updating the ICS.
Securing the ICS at the Network Level
The following best practices will help ensure that your industrial control system network is secure in the age of Industry 4.0:
- Promote Network Visibility: Through various interviews with industrial stakeholders, ABI Research has learned that network visibility is the highest ICS security priority. Industrial firms can promote network visibility by mapping the network with port scanners and network mapping software. This helps identify network topology, system configurations, and communication patterns.
- Monitor Network Data Flows: Monitoring data flows within the network is imperative to identify when malware has infiltrated the industrial control system. For example, the Stuxnet worm and the Havex Trojan malware both use data packets to attack ICSs.
- Set up Firewalls and Unidirectional Flows: Firewalls, such as Cisco’s Firepower Next-Generation Firewall and Adaptive Security Appliance (ASA), are an effective ICS security solution. Firewalls are an established market with many vendors offering ICS protection solutions. Moreover, unidirectional gateways provide better ICS security, but are substantially more expensive.
- Leverage Machine Learning (ML): Recent research into ML strategies for industrial control system security has shown promising results for intrusion detection and response in the ICS environment. This is particularly important in detecting cyberattacks in mobile cloud computing. ML-based intrusion detection and response schemes are reportedly a superior cybersecurity technique to current “rule-based” security schemes.
- Set Honey Pot Traps: In the context of ICS cybersecurity, a honeypot refers to a fake network that lures would-be attackers of the actual network. It’s important that the attacker genuinely believes the real ICS has been infiltrated. For example, the honeypot could pretend to be a PLC and enable the attacker to acquire control of it. This security best practice keeps the ICS safe by diverting the attacker’s attention from critical aspects of the system. Honeypots can either be low-interaction or high-interaction, with the latter requiring much more resources.
The Next Step in Your ICS Cybersecurity Strategy
As recent headlines allude to, industrial control systems are highly vulnerable to cyberattacks. As threat actors become smarter and more sophisticated, industrial companies and their cybersecurity service partners must leverage innovative solutions and proven ICS security best practices.
To help you on the journey, subscribe to ABI Research’s IoT Cybersecurity Research Service. Access to our global team of analysts means your organization will get its hands on Analyst Insights, various market forecasts, and long-form research reports that discuss the latest industrial security challenges, solutions, market outlooks, vendor profiles, and more.
Related Content:
- ICS Protection from Cyberthreats: What Will It Take? [Research Highlight]
- What Is Intellectual Property Theft, and How Can Manufacturers Prevent It? [blog post]






