Post-Quantum Cryptography (PQC) solutions are a must-have cybersecurity tool for organizations to safeguard against attacks from large-scale quantum computers.
Quantum computing is a blessing and a curse. On one side of the coin, quantum computing can work miracles, such as speeding up the drug discovery process or reducing carbon emissions. However, when put in the wrong hands, quantum computers can be used to devastate a society. For example, a recent study carried out by the Hudson Institute indicated that a single quantum attack targeting the Fedwire Funds Service payment system could result in as much as US$1.95 trillion in financial losses in the United States.
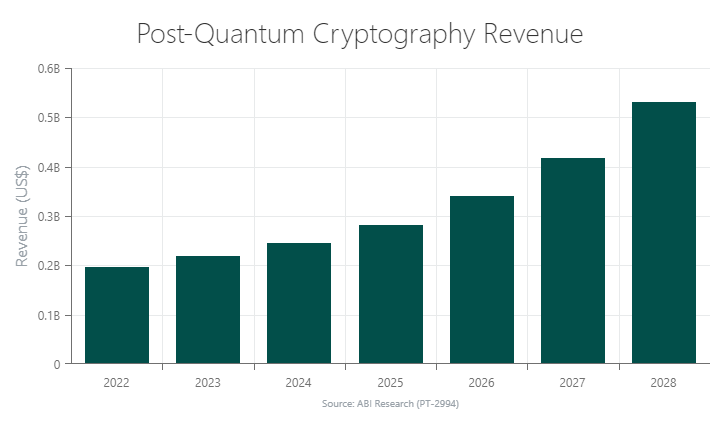
Attack-capable quantum computers are fast approaching, making PQC the next frontier of cybersecurity. As the chart below depicts, PQC will be a US$530 million market by 2028.
Why Post-Quantum Cryptography Is Needed
The purpose of Post-Quantum Cryptography (PQC) is to prevent cyberattacks carried out with large-scale quantum computers. This is accomplished by developing advanced cryptographic algorithms and systems that would be secure against a potential attack via quantum computers.
Implementing PQC is, therefore, a key prerogative for protecting digital societies around the world. Post-quantum cryptography is still very much in the early stages, which means the race is on, and standardization efforts are currently at the forefront.
Related Content: Navigating the Future of Cybersecurity with ABI Research’s Quantum-Safe Technologies Research Service
PQC Standardization Endeavors
The National Institute of Standards and Technology (NIST) has taken the lead among Standard Developments Organizations (SDOs), with several proposed standards being developed. Four of these standards—CRYSTALS-Kyber, CRYSTALS-Dilthium, SPHINCS+, and Falcon—have been officially standardized. While CRYSTALS-Kyber is a public key encryption/Key Establishment Mechanism (KEM), the other three standards are Digital Signature Algorithms (DSAs).
For NIST, the motivation now is to find PQC algorithms that can more easily be used by resource-constrained technologies, such as the Internet of Things (IoT). Moreover, PQC algorithms that work well with technologies that require low latencies, such as cyber-digital systems, are in full pursuit. A Fourth Round of standardization is in process to find additional KEMs, and a new call for additional DSA schemes has also been launched, both by NIST.
The standardization process for post-quantum cryptographic algorithms is a gradual one, taking multiple years to unfold. The PQC standardization development process involves vigorous testing in diverse environments, as well as many stakeholders, such as national/regulatory agencies, other SDOs like IETF, and various companies, industry groups, and open-source movements.
Government Support for Addressing the Quantum Threat
Addressing the post-quantum threat is seen as a matter of protecting national security, critical infrastructure, commercial interests, and citizen privacy. Consequently, a number of national policies have been proclaimed in recent years as it relates to PQC. The United States, for example, has a memorandum that outlines its commitment to migrating to quantum-resistant cryptography for cybersecurity.
In Europe, the French government announced in 2021 that it would invest €1.8 billion in its national quantum strategy for research work, with €150 million allocated to PQC specifically. Also in Europe, Germany’s federal cybersecurity authority, BSI, has endorsed a few PQC algorithms as it moves toward the future post-quantum transition.
Other national policies regarding PQC include China’s cryptography algorithm competition in 2020, Japan’s published reports on PQC, and the United Kingdom’s National Cyber Security Centre (NCSC) guidance for PQC algorithms.
Migrating to PQC Requires Crypto Agility
It’s going to be a few decades before a total post-quantum migration is established. Many enterprises lack the capability to start fresh with PQC immediately, while others simply don’t want to spend the money. In the interim, it’s going to be crucial that legacy devices and systems that don’t support PQC are still accounted for in the context of cybersecurity. As hybrid formats become the new norm, crypto agility will be integral to the continued use of PQC algorithms. Crypto agility ensures that classical crypto is protected, while encouraging the gradual transition to PQC.
In a general overview, crypto agility emphasizes the thought that current and next-generation cryptographic systems can coexist as we transition to PQC. Because PQC algorithms are new and widely untested in commercial settings, it’s imperative that new standards can swiftly be patched or replaced with better ones.
Crypto agility also extends to the market offerings for PQC products. As speculation surrounding quantum-safe technologies is muddied, crypto agility will be important in providing flexibility for consumers. That means PQC will come in different form factors and unlock a wide array of cryptographic algorithms that can be easily interchanged, used in a hybrid format, or modified/upgraded for specific circumstances.
Ultimately, crypto agility ties up two loose ends at once: it ensures that the industry is adequately prepared for newly standardized PQC algorithms, while encouraging the flexible, customizable, scalable, and upgradeable cryptographic systems that enterprise customers need during the transitional phase.
To take a deeper dive into the world of PQC and how best to mitigate the threat from attack-capable quantum computers, download ABI Research’s Post-Quantum Cryptography report. This content is part of the company’s Quantum-Safe Technologies Research Service.
Related Content:
- U.S. NIST PQC Standards to Kick-Start Product Commercialization
- Quantum Key Distribution as a Mainstay in Quantum-Safe Security: A Fine Balance
- Unite and Conquer: DigiCert and Vercara’s Unified PKI-DNS Solution Helps to Tackle the Challenges Posed by the IoT and Post-Quantum Computing
- Quantum Cryptography: The Next Frontier for Secured Communications and Satellites’ Pivotal Role
- Post Quantum Cryptography (PQC): Algorithms, NIST Standardization, Challenges, and Outlook
- Apple Pushes Post-Quantum Cryptography into the Mainstream with PQ3 Announcement
- Singapore Aspires to be Quantum-Safe Network Pioneer for Government & Financial Services