Across every sector, organizations are digitally transforming to meet customer demand, increase productivity, compensate for labor shortages, create safer work environments, and build smarter cities. This digital transformation requires wider-spread use of Internet of Things (IoT) hardware, sensors, platforms, and services, with ABI Research forecasting that there will be 40.77 billion IoT connections worldwide by 2027. However, embracing IoT devices poses an elevated cyber risk due to more network entry points to target. When it comes to addressing the growing IoT cyberthreat, three primary security solutions are prioritized by enterprises and governments: Trusted Platform Modules (TPMs), Trusted Execution Environments (TEEs), and secure Microcontroller Units (MCUs).
IoT Devices That Pose A Cybersecurity Risk
To gain a clearer understanding of where IoT cyber risks lie, ABI Research compiled Table 1, which identifies the hub devices, access points, accessories, and sensor nodes that can all be breached by a malicious actor.
Table 1: IoT Device Types by Vertical Market
(Source: ABI Research)
| End Market |
Vulnerable IoT Hub Devices and Access Points |
Vulnerable IoT Accessories and Sensor Nodes |
| Connected Car |
In-Car Infotainment/Telematics |
Others/Under the Hood (incl. Key Fobs and Accessories) |
| PCs and Digital Home IoT |
Desktop PCs; Laptops; Netbooks/Chromebooks; Ultrabooks; Consumer Access Points; Consumer External Adapters; Flat Panel TVs; Set-Top Boxes; Gaming Consoles |
PC Accessories; Printers; USB and Other External Modems; PCMCIA Cards; Gaming Console Controllers; OEM Remote Controls; 3D Glasses; Digital Photo Frames; Speakers; DVD/Blu-ray Players/Recorders |
| Smart Home IoT |
Home Automation Controllers |
Smart Home Devices; Smart Appliances; Residential Smart Lighting |
| Wearable Computing |
Other Wearables |
Health and Medical; Sports, Fitness, and Wellness Devices |
| Mobile & Telecommunications Devices |
Smartphones; Enhanced/Feature Phones; Media Tablets; Mobile Internet Devices; Cellular Routers, Gateways & Modems |
Mobile Phone Accessories; Handheld Gaming; PNDs; Digital Cameras/Camcorders; eBook Readers; Portable Media Players |
| Smart Cities and Buildings |
Enterprise Access Points |
Commercial Building Automation; Intelligent Transportation Systems; Smart Parking; Smart Street Lighting; Other Smart City Applications; Video Surveillance |
| Utilities and Industrial IoT |
Edge Devices, Aggregators (Gateways, Routers) |
Agriculture; Industrial Equipment; Hospital and Other Healthcare Equipment; Heavy Vehicles; Electricity Metering; Water and Gas Metering; Smart Grid Equipment; Renewable Energy; Aerospace; Defense |
Trusted Platform Modules
A Trusted Platform Module (TPM) is an international security specification developed and published by the Trusted Computing Group (TCG). TPMs are also microcontrollers that ensure the secure storage of artifacts (passwords, certificates, or encryption keys) used to authenticate and attest the IoT platform. By authenticating and attesting the IoT platform, one can be sure that the platform is what it claims to be and hasn’t experienced a data breach.
Market Outlook for TPMs
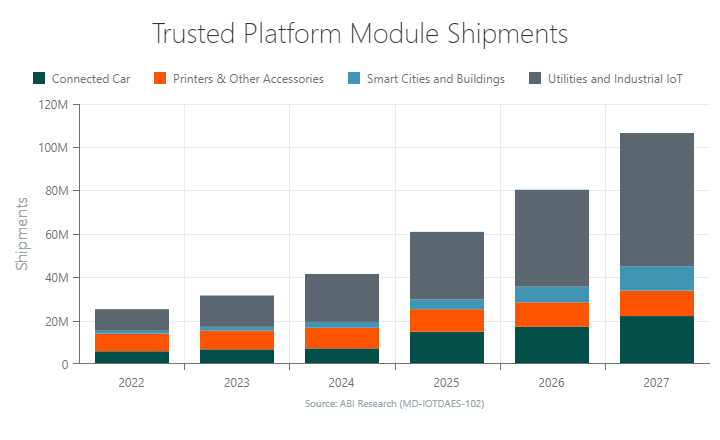
Growing at a Compound Annual Growth Rate (CAGR) of 33.4%, ABI Research forecasts annual TPM shipments to increase from 25.68 million in 2022 to 108.56 million by 2027. Demand for TPMs is primarily driven by utilities/Industrial IoT (IIoT) and connected car applications.
Revenue for TPMs will also grow at a CAGR of 33.4%, increasing from US$7.70 million in 2022 to US$32.57 million in 2027
Trusted Execution Environments
When ABI Research refers to Trusted Execution Environments (TEEs), we refer to a secure area of the main processor in IoT-connected devices, such as smartphones. A TEE provides users with a trusted, siloed environment within the IoT device that ensures sensitive data storage, processing, and protection. Moreover, a TEE’s “trusted applications” software facilitates end-to-end security by applying protected execution of authenticated code, confidentiality, authenticity, privacy, system integrity, and data access rights.
Market Outlook for TEEs
For the TEE section of our IoT cybersecurity market forecasts, ABI Research expects shipments to grow at a CAGR of 42%, from 82.95 million in 2022 to 483.95 million in 2027. The largest segment, by far, for TEEs comes from utilities/IIoT, accounting for 35% of global shipments in 2027. However, smart cities & buildings, as well as wearable computing, are significant market drivers for TEEs, too.
By 2027, TEE revenue is expected to be 5.5X greater than in 2022. Our Digital Authentication and Embedded Security: IoT Cybersecurity market data report shows that revenue tied to TEE purchases will soar from US$60.55 million in 2022 to US$333.92 million in 2027.
Secure Microcontroller Units
ABI Research defines a secure Microcontroller Unit (MCU) as a tamper-resistant microcontroller that comes with dedicated encryption engines, libraries, and True Random Number Generators (TRNGs), in addition to secure Non-Volatile (NV) storage. Further, secure MCUs allow for secure communication, key/certificate protection, and hash functions for IoT device authentication and Intellectual Property (IP) protection.
The class of MCUs we evaluate are tailored to low-end IoT applications; therefore, they use minimal resources and are discrete. A secure MCU is essentially a beefed-up version of other authentication Integrated Circuits (ICs) because Information Technology (IT) and Operational Technology (OT) teams can program the cybersecurity software to execute specific tasks.
Market Outlook for Secure MCUs
ABI Research anticipates that secure MCU shipments will grow at a CAGR of 29%, increasing from 814.88 million in 2022 to 2.88 billion by 2027. That is a more than a threefold increase. Demand is stimulated significantly by retail, advertising, and supply chain IoT applications, encompassing 41% of all MCU shipments in 2027.
Meanwhile, the revenue opportunity associated with secure MCUs easily outweighs the revenue opportunity for TPMs and TEEs. By 2027, secure MCUs will generate US$5.47 billion in revenue, up from US$1.71 billion in 2022.
Get in Touch with Us
The world of IoT cybersecurity is always changing, with new technologies and market trends constantly shifting industry dynamics. Preventing IoT cyberthreats requires organizations to have access to the most current and accurate insights into best practices and novel solutions. And for technology vendors, it’s essential to identify the most promising segments to optimally develop product portfolios. If you and your organization could benefit from these kinds of deliverables, subscribe to ABI Research’s IoT Cybersecurity Research Service today!
Related Content:







