Recent Government Conference Reveals SBOM Embrace, but Also Challenges
|
NEWS
|
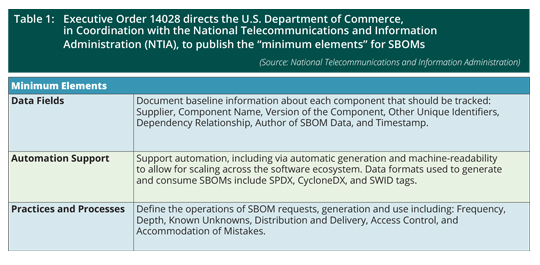
Private sector attendees at a recent Cybersecurity and Infrastructure Security Agency (CISA) “SBOM-a-Rama” conference emphasized the need to embrace implementing SBOMs to maintain software supply chain security and integrity, yet also displayed concern over the challenges facing SBOM adoption. Various industries, including the health, auto, and defense sectors, agree that SBOMs are essential for ongoing vulnerability and threat management due to the increasing usage of open-source libraries (Open Source Software (OSS)) and third-party code in today’s software products. This means cybersecurity teams need to deploy SBOMs to understand the “ingredients” of their software supply chains in order to address vulnerabilities. In addition to security considerations, those vendors that sell software products, including the devices that deploy them, to the U.S. defense sector or government, are obliged to "publish minimum elements for an SBOM” under Executive Order (EO) 14028, known famously as the Cybersecurity EO.
Yet many cybersecurity practitioners believe that the current CISA and government guidelines are not enough for SBOM adoption. The challenges include the lack of a common framework for SBOM transmission, and the exact breadth of the information that needs to be disclosed in an SBOM. Other challenges include uncertainty over who should lead the effort for standardization and transparency in SBOM execution—the federal government or the private sector. While these types of concerns persist, SBOM service providers told ABI Research that they believe the difficulties are because of the first days of a new technology landscape, and that new guidelines and more detailed implementation are on their way. Also, sectors like the healthcare industry are already widely deploying SBOM services due to their dependence on lifesaving devices with embedded software. The overall environment indicates that other sectors will eventually follow and embrace SBOM services.
New Business Opportunities, More Transparency
|
IMPACT
|
Vendors talking to ABI Research maintain that the organizations across various sectors that have deployed SBOM implementation are more agile to respond to threats, or address threats such as vulnerabilities in the Log4j 2 Java library that is used to log error messages in applications. Attackers can remotely control Internet-connected devices if the zero-day vulnerability is not addressed. SBOMs help organizations and software developers identify, update, or patch vulnerability in the software supply chain. The cybersecurity benefits of a clear picture of the software supply chain means more developers, executives, and security officers who want insight into their software products will seek SBOM services to properly generate, manage, and keep track of their software components. Emerging regulatory requirements, such as EO 14028, and SBOM requirements for government contractors and vendors selling software products to the defense sector will significantly boost the services related to both SBOM generation and SBOM analysis. Further pushing SBOM regulation, ergo related businesses, is Article 37 of the proposed (yet to be passed) European Cyber Resilience Act that explicitly states that “manufacturers should identify and document components contained in the products with digital elements, including by drawing up a software bill of materials.”
SBOM Services Provide New Opportunities for Software Developers, Especially in Health and Defense
|
RECOMMENDATIONS
|
The software consumer market is still in the early stages of embracing SBOMs, yet in a universe with an increasing number of connected devices that are also software dependent, leveraging SBOMs for digital supply chain resilience will soon become imperative. The software consumer market will eventually become the largest segment of the SBOM market, but for now, software producers are the main consumers of SBOM services. These services include detailed SBOM generation that goes beyond the minimum requirements of NTIA, but more importantly, involve SBOM analysis where a generated SBOM (by the software vendor) is constantly analyzed for threats by SBOM service providers. While a variety of open-source tools can help generate SBOMs for free, or for a relatively low-cost fee, SBOM analysis and software lifecycle management is a different story, requiring specialized knowledge and technology, and therefore, a promising business proposition for early entrants into the SBOM services market.
The future course of the market, particularly if SBOM service vendors specialize in specific sectors, remains to be determined. Some experts argue that the different threats facing different industrial sectors mean there will be SBOM services tailored to those sectors, while others point to the common nature of SBOM analysis to argue that the future of SBOM management will not be sector agnostic.
For the time being, vendors could be broadly categorized as SBOM generators, and SBOM management platforms or service providers. This could change as more partnerships forge to streamline detailed SBOM generation with SBOM threat detection and management capabilities. One thing is for sure: SBOM implementation and services are in their early stages, and so are the benefits of SBOM deployment. Nevertheless, both early adopters and service providers will benefit from a timely entrance into the market. Enablers will benefit from market opportunities that the first-mover advantage brings, while consumers will benefit from more resilient software products and better insights into their software supply chains.

