Exchange Server Hack
|
NEWS
|
Microsoft stated that its Exchange Server was hacked during Q1 2021. The MS Exchange Server is responsible for email, calendar, and collaboration platform services available across web-based systems, desktops, and mobile devices containing a wealth of information. According to Microsoft’s Threat Intelligence Center as mentioned by its Corporate Vice President, Tom Burt, the company claimed that a state-sponsored group of cyber-attackers from China, called HAFNIUM, were responsible for the attack. The news was picked up by large news agencies like Bloomberg and Washington Post, which stated that other large entities like the European Banking Authority may also have been compromised. Other news agencies like the Global Times quote different research stating that cyber-attacks on Chinese organizations have radically increased over the years, making China the true victim here.
Focusing on the security insights, and putting politics aside, what should organizations gather from this?
Politics Aside, What Should We Gather from This?
|
IMPACT
|
The attack and its aftermath: Microsoft’s Threat Intelligence Center stated that the HAFNIUM attackers leveraged legitimate open-source frameworks, like Covenant Open-Source, for command-and-control attacks towards various internet-facing servers. Once they managed to secure a foothold on victims’ networks, they exfiltrated data to file-sharing online platforms like MEGA which, perhaps ironically in this instance, boasts secure cloud data storage and rapid data transfers.
Custom-tailored regional security offerings: Cyber-attacks on major corporations that manage to attract the industry’s spotlight are bound to have a great effect in the long-term and will undeniably boost cloud and data protection service revenues. The fact that this incident was also tagged with a “state-sponsored attack” connotation is expected to drive additional regional effects, such as increased demand for managed security services and customizable security offerings, and potentially even add towards regional regulatory measures in the long-term. Other leading organizations are already ahead. Siemens, for example, is already positioning its managed cyber-security offerings on Chinese organizations, stating that they are increasingly being targeted across the board in its key applications, ranging from industrial and manufacturing to retail and online payments.
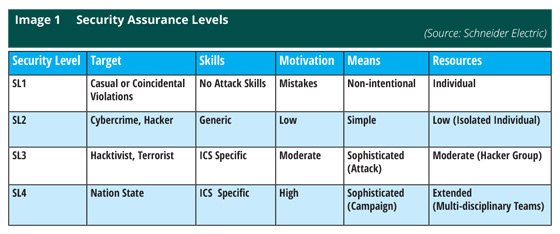
Ranking system by Schneider Electric: Industrial and manufacturing security is undeniably going to be the most attractive target market in China. Schneider Electric has created its own ranking system for attacks on industrial control systems (shown in Image 1), ranging from simple violations to hacktivism, terrorist cyber-attacks, and nation-state high threat attacks. A complete overview of cyber-security in ICS can be found in ABI Research’s Cybersecurity for Industrial Control Systems Analysis Report (AN-2484).
Cyber-agendas and State Objectives
|
RECOMMENDATIONS
|
Everyone is an attacker, everyone is a victim: To avoid getting caught in any political quagmire and focus on the reality of the current state of the “cyber-warfare market”, it is important to clear the air around the cyber-espionage and state-sponsored attacks. Pure-play cybersecurity providers like Kaspersky, Symantec, and FireEye regularly compile heat maps of the largest threat actors (and victims). Hacker groups from the United States, China, India, Israel, France, and the United Kingdom usually top these charts every year. Therefore, focusing on isolated incidents of state-sponsored attacks will not provide any valuable information, and a global view and evolution over the years would be more productive. Unsurprisingly, these countries are actively involved in cyberwarfare, but the interest would be in which areas cyber-attacks are targeted towards and which agenda they support.
Cyber-agendas—what can we learn from state-sponsored attacks?: State-sponsored attacks are orders of magnitude more important than standard monetary-driven hacker , since attackers have specific objectives set to disrupt operations, surveil and siphon information from critical or high-value systems, and are usually in an effort to support other state clandestine objectives. Although there is a huge list of application-specific attacks, in general they can be clustered in the following key areas:
- Political and governmental—obtaining high-level individual secrets or governmental projects
- Commercial and enterprise—amassing market secrets and potentially stealing technological innovations
- Financial and banking systems—gathering monetary intelligence and applying pressure on financial systems
- Critical infrastructure—crippling energy and telecommunications (which also fits into military-focused cyber-attacks)
- Industrial and manufacturing--disrupting production which equates into a chain-reaction into other applications inside or even outside borders
Long-term goals: These should include extrapolating insights based on a discovered target (e.g., the Microsoft Exchange Server attack) and information on the interests that this target might serve in both the short and long term. There are numerous state objectives. While the Stuxnet attack on Iran’s nuclear facilities is often quoted as a first example of state sponsored attack against industrial systems, there are many more current examples. Russia has been accused of a series of cyber-attacks on Ukraine starting back in 2017, originating from the introduction of the Petya malware. Attacks varied and escalated from targeting simple supermarket chains and retail to critical infrastructure and energy substations, leading to current events: military armed forces actually invading Ukraine soil.
This goes to show in real terms what cyber-warfare can actually accomplish and how security vendors should hope to tailor and quite possibly even market their services. Using historical cyber-forensics data and advanced analytics security alongside the use of sophisticated security information and event managements (SIEMs) and managed security services (MSEs), organizations can hope to hold a decent security posture. However, most small and medium businesses (SMBs) lack the capital to invest in such security tools. To that end, cybersecurity vendors can strategize towards better SMB offerings and offering cost-effective solutions through versatile cloud or semi-managed options. This can help at the very least to minimize the risk of state-sponsored attacks and definitely provide the shot in the arm the industry requires.
