1Q 2023 | IN-6832
Registered users can unlock up to five pieces of premium content each month.
Vice Society Ransomware Gang Now Aiming at the Industrial Sector, Deploying Advanced Encryption |
NEWS |
Cybersecurity software company Trend Micro announced ransomware group Vice Society is targeting the manufacturing sector in countries including Switzerland, Argentina, Israel, and Brazil. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) issued a joint Cybersecurity Advisory (CSA) in September 2022 warning about the group’s activities. The CSA indicated that the group is “disproportionately targeting the education sector with ransomware attacks,” but recent findings reveal Vice Society is widening its target perimeter to include industrial operations.
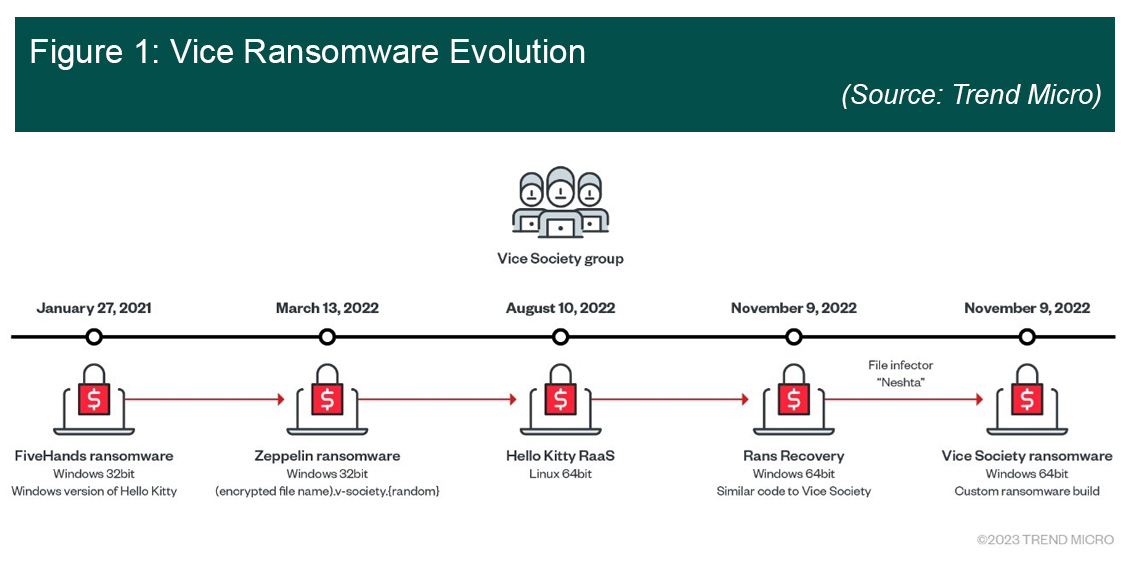
In the past, the group exploited the PrintNightmare vulnerability which affected the Microsoft Windows (MS) Operating System (OS) allowing attackers to gain system-level access to vulnerable systems including domain controllers and active directory admin servers. The group also deploys versions of Hello Kitty/Five Hands and Zeppelin ransomware. Zeppelin allows attackers to gain access to victims’ networks via Remote Desktop Protocol (RDP) exploitation, while Hello Kitty/Five Hands seals and encrypts files after access through Windows Restart Manager. These are pre-existing third-party ransomware that are sold on the DarkWeb, indicating that until now the group did do not use a ransomware variant of unique origin. The new findings mean the group may be changing strategy by shifting toward developing custom-built ransomware and adopting stronger encryption. Per Trend Micro, this means the group is “preparing for its own Ransomware-as-a-Service (RaaS) operation”. Coupled with the groups tendency to target backups and exfiltrate data for double extortion, the new development points to a more aggressive strategy that could threaten industrial organizations.
Threats Looming: Inadequate Cyber Security Budgets, The Rise of Sophisticated Attacks |
IMPACT |
Vice Society’s expanding and assorted threats come at a time when only about half of companies have proper funds to effectively counter cyberthreats. A recent Neustar International Security Council (NISC) survey of 304 senior-level executives in the United Sates, the European Union, Africa, and the Middle East indicated that 44% stated they will experience cybersecurity budget cuts or stagnation in 2023 due to macroeconomic trends and concerns over recession. Based on the survey, 51% of companies said they had inadequate budgets to counter cyberthreats. While budget constraints will hamper cybersecurity efforts and impact mitigation, the nature of cyberattacks are becoming increasingly sophisticated. Budget constraints were third on the list of executive cyber concerns, with 35% of managers describing it as their concern, while 60% of respondents indicate their number one concern is the increased sophistication of cyberattacks. Cybercriminals recently even deceived federal employees, gaining remote access to monitoring and management software to then steal money from bank accounts. The expansion of attack vectors and the increasing sophistication of attacks, along with stagnant cybersecurity budgets, imply a high-risk cyber environment in 2023. Industrial operators are likely to be even less prepared than other enterprises, because of not adopting mitigation measures such as zero-trust strategies and low levels of investment in OT security. Vice’s deployment of custom ransomware could indicate heightened attacks on critical infrastructure, like a recent alleged attack by the group on the San Francisco Bay Area Rapid Transit system last month where the transit agency’s police department data was exposed. The development of in-house ransomware could also indicate the group plans to target proprietary or obscure systems, commonly used in industrial settings.
Organizations Need to Prioritize Threat Assessment, Turn to Cybersecurity as a Service (CSaaS) |
RECOMMENDATIONS |
Companies with budget constraints may find outsourcing their cybersecurity to a specialized provider as a way to handle both rising costs and maintaining their security. Security providers have more experience, and constantly monitor the evolution of cybergangs such as Vice Society. Delegating cybersecurity to specialized providers leads to concentration on core business or industrial operations. Moreover, in highly regulated industrial settings, cybersecurity providers can ensure compliance to regulatory measures that are constantly evolving. Industrial operators, on the other hand, will have to ensure they provide a deep understanding of their complex industrial environment to providers. Security providers working with industrial clients need to understand their customer’s needs and the specific demands of Operation Technology (OT)-Information Technology (IT) interactions in industrial settings. With the increasing adoption of Industry 4.0, namely high-tech connected Internet of Things (IoT) devices and the convergence of physical and IT technologies, the landscape of malware attacks will expand and continuously evolve to become more sophisticated, including autonomous zero-day exploits that do not need human intervention to spread into affected systems. This could provide an opportunity for security vendors to better position themselves in industrial markets, especially regarding highly in-demand network security solutions.