4Q 2023 | IN-7192
Registered users can unlock up to five pieces of premium content each month.
70% of Iran's Gasoline Stations Are Knocked Out Due to Massive Cyberattack |
NEWS |
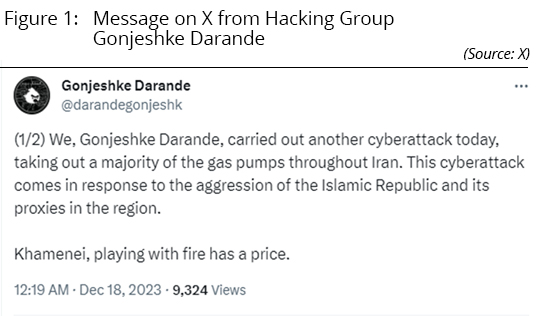
The hacking group “Gonjeshke Darande” or the Predatory Sparrow launched a massive cyberattack against Iran’s state-run gas stations, knocking out 70% of the country’s pumps. Echoing geopolitical tensions in the Middle East region, the group declared in statements both in Farsi and English that “this cyberattack comes in response to the aggression of the Islamic Republic and its proxies in the region.” Gonjeshke Darande claimed the attack was only a hint of its capabilities and that it was “just a taste of what we have in store.” The group declared it could have stopped all gas stations in the country, but as a humanitarian gesture and “to limit potential damage to emergency services,” allowed the operation of 30% of pumps. "A month ago we warned you that we’re back and that we will impose cost for your provocations," the group added.
Iran has witnessed a series of industrial incidents, including fires in oil facilities and industrial plants in recent years. The incidents are often attributed to disregard for adequate cyber defenses and outdated technologies. In the past, Gonjeshke Darande and hacking group GhostSec have been accused of breaching the computer networks of major Iranians steel companies leading to massive fires. Gonjeshke Darande even posted a video of an explosion at a steel mill in Iran in 2022.
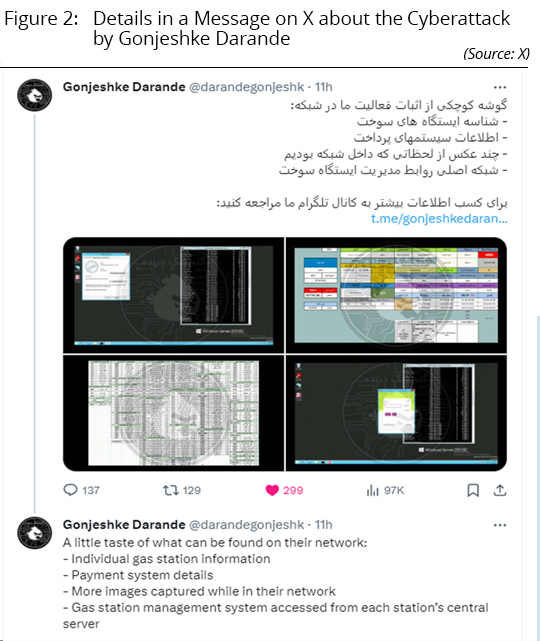
In the recent attack, the group tweeted that it not only disrupted the flow of gasoline, but was able to extract data from gasoline station networks and their central server, including information on payment systems.
As a result of the attack, long lines were formed outside fuel stations in the capital city of Tehran, while the government immediately called for a “crisis committee” to address disruptions.

Lessons to Be Learned: Cyberattacks Could Have Real Physical Consequences |
IMPACT |
Iran’s unique position because of long international sanctions provides a natural experiment for examining cyberattacks against critical infrastructure. Due to sanctions, the country has difficulty procuring up-to-date hardware and software technologies, and often relies on Chinese manufactured electronics. Moreover, because the country deploys older systems, it can no longer update its legacy systems with security patches. The country also uses pirated Operation Systems (OSs), including Windows, providing a facilitating environment for cyberattacks. As the Iranian attack indicates, attackers prefer to choose visible and salient industries that can deliver more credit and increased recognition for them, such as critical infrastructure, heavy industries, and impactful services like energy distribution centers.
Iran’s Oil Minister Javad Owji blamed Israel and the United States for the attacks. This could be a sign of escalating retaliatory hacks. Iranian state-sponsored hackers regularly target Western and Israeli targets, including water systems and hospitals in Israel. The attack could prompt them to intensify their activities. Western companies with government contracts, or those with significant presence in the Middle East and Israel could be potential targets for retaliatory attacks.
Industrial Operators Should Be Cognizant of Retaliatory Attacks to Gain Control of ICS |
RECOMMENDATIONS |
Companies with Internet access to their Operations Technology (OT) equipment should be especially vigilant and take appropriate measures, including implementing heightened access and remote-work credential security. Industrial firms should be especially vigilant at times of heightened socioeconomic tensions as the threats of unpreparedness exposes them to more risk. Malicious actors can weaponize OT systems to harm or even kill humans. The cost of such attacks is immense and could result in irreparable brand damage and soaring insurance costs for breached entities. Iranian state-sponsored hackers will prefer to conduct attacks, gaining access to Industrial Control Systems (ICSs), instead of ransomware attacks where money is the main motive.